Hey guys, Here is the new information for you your simcard in your pocket is a damn tiny CPU lets check it out.
The Subscriber Identity Module (SIM) was first introduced by the GSMA in 1987 in a farsighted move to ensure that a mobile subscriber on a GSM cellular network could maintain an identity on the network independant of a particular mobile device.
While its visibility has decreased over time, the humble SIM has been an essential part of mobile devices ever since. Today, thirty years after the GSM standard was published, you might be forgiven for forgetting about them entirely—they work so well that it’s easy to overlook their existence. Nano SIMs are so small that they barely qualify as being consumer-accessible anymore and devices such as Amazon’s Kindle and connected cars don’t even bother to make them user-accessible at all.
But regardless of the physical form, SIM's have withstood the test of time and are here for the foreseeable future. About five billion of them are produced every year, so it’s worth taking a look at exactly what they are, especially given that some of their abilities are quite surprising.
The small but controlling type
Did you know, for example, that a SIM can run apps and communicate over the mobile network entirely independently of the host phone? Or that the SIM is arguably more in control of the phone baseband than the phone’s “main” operating system? Or that SIMs can support TCP/IP and run a web server? Read on!
>>History
As mentioned in the introduction, the SIM was part of the GSM standard since the very beginning.
Over the intervening years much has changed. The most obvious change that has taken place is the physical form of the cards themselves from a credit-card sized object, or Full-size SIM, all the way down to a nano-SIM, over forty times smaller.
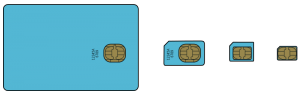
Standard SIM sizes (image from Cvdr based on Justin Ormont’s work, CC BY-SA 3.0)
The four SIM sizes are:
- full-size—the size of a credit card, or 85.60 × 53.98 × 0.76 mm
- mini—the first “normal” SIM card and the most popular format for much of the history of GSM
- micro—an attempt to reduced the size of the mini SIM, quickly obsoleted by the nano SIM
- nano—today’s standard size, the smallest possible SIM that retains the same contact pads of the original specification. 12.3 × 8.8 × 0.67 mm
Thoughtfully, the size specification for the Nano SIM is fractionally thinner as well as shorter and narrower than all of the predecessors, allowing it to be placed in a fully enclosing adaptor to fit the bigger size slots.
In addition to physical changes, SIMs have changed their operating voltages over the years. The three supported operating voltages for SIM cards are 5 V, 3 V and 1.8 V. The operating voltage of the majority of SIM cards launched before 1998 was 5 V. Subsequently produced SIM cards are compatible with 3 V and 5 V. Modern cards support 5 V, 3 V and 1.8 V.
It’s a testament to the GSM that its design has stood the test of time in the face of the extraordinary changes in the surrounding landscape. A contemporary SIM card will still work in a decade-old device.
The SIM is not unique to GSM networks—other cellular telephony standards have copied the approach e.g. R-UIMs for cdmaOne/CDMA2000 and Iridium. CMDA2000 and cdmaOne were a set cellular standards that competed with GSM; Iridium is an ambitious satellite phone system launched in 1998, and still in use today, primarily by military customers.
>>SIM capabilities and roles
We tend to think of the SIM as being merely an ID card of sorts, a physical packaging of a subscriber ID, but there is a lot more to them than this.
The vast majority of SIMs today are in fact Universal Integrated Circuit Cards (UICC) that implement Oracle’s Java Card standard, a smart card specification. As such, SIMs are complete computing platforms with a CPU, RAM, persistent storage and connectivity that can run specially targeted apps coded in Java.
The core duty of SIMs is to authenticate the mobile device with the network (and not, notably, the other way around). What we think of as subscriber IDs on the SIM are in fact applications, run on demand by the onboard CPU. A SIM might have any of the following identity applications on it, depending on operator requirements:
- GSM / SIM – used by GSM networks
- CSIM – used in CDMA2000 networks
- USIM – used in UMTS 3G/4G Networks.
- ISIM – The IP multimedia Services Identity Module (ISIM) application might be found on modern cards for 3G/LTE which are based on GlobalPlatform version 3
For the particular case of GSM, the card contains the unique subscriber number (IMSI, International Mobile Subscriber Identity), the secret authentication key and other properties used to authenticate to the network and uniquely identify the card’s owner.
In addition to this core duty SIMs have many additional capabilities. Initially these capabilities were centered around network connectivity. As an example, the SIM stores a list of mobile network codes (MNCs) for preferred mobile operators, used when roaming out of the home network, conferring an affinity for certain networks to your device.
SIMs can store contact details and SMS messages but this feature is of less interest today as phones are increasingly backed up remotely and it’s ever-easier to transfer data such as contacts and messages between them when upgrading.
>>SIM Toolkit
The SIM Toolkit (STK) standard was developed by operators to facilitate the provisioning of value added services to mobile subscribers. This represented a significant shift in the role of the SIM from its quiet background authentication duties to that of hosting user-visible applications. These applications are used to implement user features such as prepaid balance queries, money transfer (M-Pesa) and call-fowarding set up.
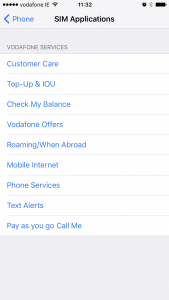
SIM Toolkit apps from Vodafone
On iOS you can find these apps listed in Settings | Phone | Sim Applications. On Android there is usually an icon that launches the menu of SIM apps in the main applications drawer.
STK app menu on iOS STK app menu on Android
Modern smartphone apps offer a far richer user experience than SIM apps so these have largely fallen out of use except in territories where smartphones are less prevalent.
Historically smartcards operated by responding to queries from the handset but in addition to exposing user-visible apps, the SIM Toolkit standard also expanded the role of the SIM by allowing it to request services of the handset. The following services are supported:
- Send an SMS/MMS message
- Initiate a call
- Display a message on handset screen
- Display a menu on handset screen
- Query handset features
- Send USSD message
- Send DTMF sound
- Launch browser
- Open TCP/IP communications channel
- Allow/disallow calls
These relatively simple capabilities are sufficient to build a wide variety of applications.
SIMs can run both user-visible and background applications. Of the two, background applications are perhaps more interesting in today’s environment. SIM background applications are based on requesting notifications for events that take place on the host handset. These applications are normally dormant and activated in response to events on the host device. The UICC standard requires the following events to be supported:
- MT Call event (incoming call)
- Call Connected event
- Call Disconnected event
- Location Status event
- User Activity event
- Idle Screen Available event
- Language Selection Status event
- Browser Termination event
- Data Available event
- Channel Status event
- HCI Connectivity event (in case of NFC device)
- Access Technology Change event
- Network Search Mode Change event
This set of event notifications confers significant power to the humble SIM. With applications set up to respond to these event notifications SIMs can react to essentially every meaningful event that takes place on the host device. As an example, a SIM-based QoS application installed by an operator can respond to every call disconnect event and send an SMS to the operator with key information such as cell ID, signal strength and call duration.
The LTE guidelines for UICC implementors lists additional requirements such as a Geographical Location Request, requiring the device to “send geographical GPS information to the UICC providing the device has this capability”.
As a side note, it doesn’t take much imagination to see how useful these capabilities could be to spy agencies, particularly given their cross-platform nature, invisible operation and silent remote installation capability. You can’t see what your SIM is doing, nor can you control it.
>>SIM & handset interaction
In order to perform its core function a SIM clearly needs to be able to communicate with its host device. This is achieved with a serial communication protocol defined by ISO 7819, a smart card standard. There are four protocols in use to transfer data:
- TPDU (transmission protocol data unit) This is the base smart card standard protocol for sending and receiving data over the serial connection. A modern SIM supports four or more ongoing transactions at one time, these are managed by channels
- APDU (application protocol data unit) APDU is a transactional higher level protocol which piggybacks on-top of TPDU to save space (not following the OSI layered style). Normally a smart card is a slave unit, here meaning it is the mobile device that sends commands to the SIM. But the SIM cards are highly active entities so a scheme was implemented to work around this limitation called proactive commands. Basically the handset polls the SIM regularly and the SIM then responds with what, if anything, it wants to be done. The handset processes the request and makes a transaction back to the SIM telling it the result. This can be made asynchronously.
- JCRMI (Java Card RMI) RMI calls can be made from a Java based host (client) to the smart card (server). The RMI data is encapsulated inside APDU commands.
- Web Services (Java Card 3 and later only) Java Card 3 introduces modern SOAP/REST style communication over TCP/IP which makes life much easier for developers.
>>Smart card web server
One particularly interesting capability of SIM cards is the SIMalliance’s Smart Card Web Server (SCWS) project, standardised by the Open Mobile Alliance (OMA). This set of standards specifies a HTTP 1.1 web server capability for SIM cards, allowing them to host cross-platform web applications directly from the card itself. Both dynamic and static web pages are possible and the underlying OTA update capability of SIMs means that applications could be updated by the operator over time.
Ultimately this technology didn’t gain much traction, with scarcely a mention of it since about 2009, probably due to the explosion of native apps that started around the time that the technology was introduced. It nonetheless makes for a tantalizing vision of an alternate reality with offline-capable web apps, remotely updateable, without today’s native app silos.
>>OTA provisioning
Most modern SIM cards and phones allow for secure OTA downloading and upgrading of SIM applications. In fact the entire SIM card is effectively remotely managed by the operator. There is much thought and planning behind this since it is vital to ensure that the target SIMs have adequate storage, support the new updates and so on. It is interesting to note that the GSMA had anticipated the need for remote management a very long time ago, a salutory reminder to today’s manufacturers of connected devices which have been co-opted into launching DDOS attacks, with no means to update them once they have left the factory.
Application and configuration updates can be pushed silently to the SIM card by the mobile operator and, as with most things related to the SIM, the consumer nor the “main” phone OS is none the wiser.
>>Security
Given the power bestowed onto SIMs, security is very important. Unlike many more recently released connected devices, security has been given much consideration by the standards bodies involved. In effect, SIM security is set up to ensure that only the card issuer can load apps onto the cards.
That said, much of the GSM standards was done literally decades ago and in the meantime the march of technology has been chipping away at the assumptions made. As an example, the GSM standard insists that the handset authenticates with the network, but makes no such demands of the network since it was assumed that only a mobile operator would have the wherewithal to operate a cell tower. Fake base stations are now common and well within reach of individuals. Equally, the DES encryption algorithm initially used is now considered obsolete—advances in computing power mean that it can be brute forced fairly readily.
>>Relevance for web & app developers
For native app and web app developers, SIM-based applications present a challenging prospect. SIM application development requires knowledge of a much more esoteric set of skills than developers are accustomed to. Developers must know the extremely restricted Java Card intimately and be comfortable with the severely limited resources available on the SIM. Testing and deployment are also far more difficult because mobile operators are necessarily involved in any public deployment and there are barriers to be crossed. Tooling is generations behind the state of the art and online documentation is very thin indeed.
That said, SIM applications are extremely powerful tools given their vast reach and low-level access to the device’s hardware. They are not limited to smartphones and can be deployed silently to millions of phones without any user interaction. This means that they lend themselves well to applications such as quality-of-service measurement where operators need information about dropped calls, signal strength and so on, regardless of phone type and without having to interrupt normal user flows.
>>Future
We are accustomed to the SIM being a physical object. That looks set to change in the near future with the advent of the eSIM standard. In an era when consumers expect to be able to take underwater selfies, device manufactures are keen to rid themselves of the requirement to remove a significant opening in the device case, particularly one that requires a tiny, difficult-to-seal drawer. Thus it seems inevitable that the physical SIM will eventually relent to pressure and be subsumed into the host device.
First let’s dispel a myth. The ‘e’ in eSIM is often assumed to mean “electronic” giving rise to qualms about loosing the ability to separate a subscribers identity from a device. In fact the ‘e’ in eSIM stands for embedded: the eSIM is really just a normal SIM that happens to be directly embedded into the phone. It is still a distinct physical entity, isolated from the rest of the phone and retains all of its existing features.
One other aspect worth considering is whether SIM cards can be co-opted into DDOS duty by malefactors. Karl Koscher and Eric Butler mentioned this idea in their DEF CON 21 talk. SIMs are the perfect vector for a DDOS attack since neither the user nor the phone operating system will have any idea of what’s going on, nor any ability to do anything about it.
Is it possible? Yes. Fake mobile cells (Stingrays) are already in widespread use by law enforcement and spy agencies. Hacker versions of the same thing are readily implementable for just hundreds of dollars, an unimaginable prospect in the early days of GSM. So communicating with the device in question is eminently doable. The remaining hurdle is ensuring that the applications are accepted by the target SIMs, which requires working with the encryption mechanisms that are in place. Unfortunately, the 70s-era DES cipher that is still in use by some operators is crackable within days using FPGA clusters, and far faster if rainbow tables are available. This means that a malefactor can send correctly-signed Java applets to SIMs relatively easily, and these apps can do anything outlined above e.g. sending messages and making calls. This bad situation is compounded by the fact that the Java security fences that are supposed to prevent apps accessing the other elements of the SIM are known to be defective on some cards, potentially allowing SIM card cloning and accessing other credentials.
Perhaps the only reason that we haven’t seen anything like this happening yet is that the skills required are still fairly esoteric and getting access to a large number of devices is relatively difficult compared with other current malware techniques. The best mitigation will be a move to stronger encryption standards on SIMs.
>>Further reading
The following are some of the better pages and documents I found while researching this article.
- An introduction to SIM card application development—a very comprehensive introduction to SIMs and how to write applications for them by Peter Edsbäcker
- SIM Toolkit In Practice—another very detailed and technical overview of SIM technology and SIM Toolkit in particular, by Sjors Gielen
- UICC Device Implementation Guidelines—UICC reference from the SIMalliance
- SIM Card Web Service specification—another reference from the SIMalliance
- The Blackbox in Your Phone—deep technical details on the hardware and software of the SIM from a CCC Camp presentation in 2011 by “Hunz”.
- simhacks.github.io—repository of SIM tools and guides
Thank you, for reading and stay tuned for more information till then Enjoy life








/cdn.vox-cdn.com/uploads/chorus_image/image/57817977/Screen_Shot_2017_11_29_at_8.29.28_AM.0.png)





/https%3A%2F%2Fblueprint-api-production.s3.amazonaws.com%2Fuploads%2Fcard%2Fimage%2F859832%2F359fc858-fb61-4ddf-b6c7-fce25129e8d4.jpg)


